Step 1: Create Your CSR in IIS 7 on Windows Server 2008
- From the Windows Start menu, search for Internet Information Services (IIS) Manager and open it.
- Click Administrative Tools >> Internet Information Services (IIS) Manager).
- In the Connections pane, locate and click the server.
- In the server Home page under the IIS section >> Double-click Server Certificates.
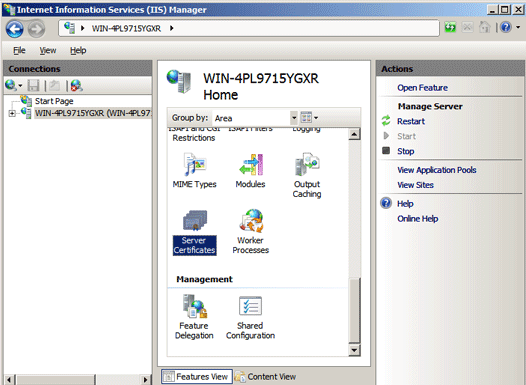
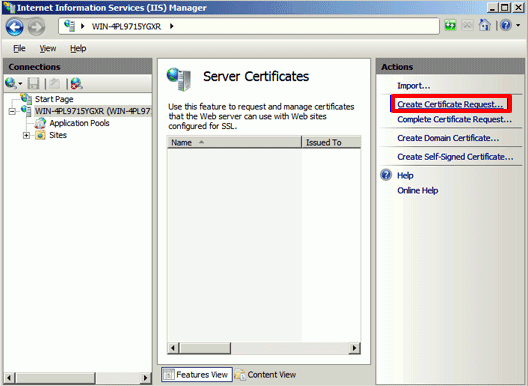
- In the Actions menu >> click Create Certificate Request.
- In the Request Certificate wizard, on the Distinguished Name Properties page, provide the information specified below and then click Next.
| Common name: | The fully-qualified domain name (FQDN) (e.g., www.example.com). |
| Organization: | Your company’s legally registered name (e.g., YourCompany, Inc.). |
| Organizational unit: | The name of your department within the organization. This entry will usually be listed as “IT”, “Web Security”, or is simply left blank. |
| City/locality: | The city where your company is legally located. |
| State/province: | The state/province where your company is legally located. |
| Country/region: | The country/region where your company is legally located. Use the drop-down list to select your country. |
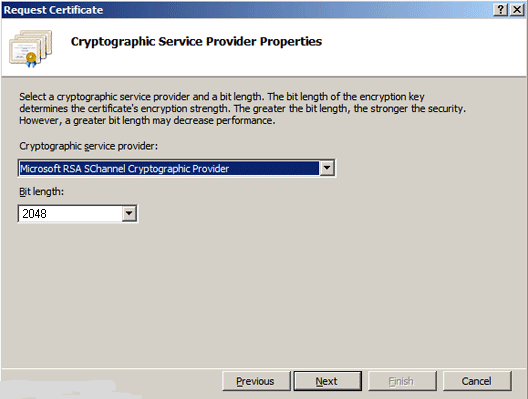
- On the Cryptographic Service Provider Properties page, provide the information specified below and then click Next.
| Cryptographic service provider: | In the drop-down list, select Microsoft RSA SChannel Cryptographic Provider (unless you have a specific cryptographic provider). |
| Bit length: | In the drop-down list, select 2048 (unless you have a specific reason for using a larger bit length). |
- On the File Name page, under Specify a file name for the certificate request, click the … button to specify a save location for your CSR.
Note: Remember the filename and save location of your CSR file. If you enter a filename without specifying a location, your CSR will be saved to C:\Windows\System32.
- Click Finish.
Step 2: After CSR generation provide the CSR to SSL certificate provider. They will provide you verification method to complete verification process.
Step 3: Once you have completed the verification process, the SSL provider will provide you with the SSL certificate file.
Step 4 : Install and Configure SSL Certificate in IIS 7 on Windows Server 2008
- On the server where you created the CSR, save the SSL certificate .cer file (e.g., yourdomaincom.cer) that you received from SSL provider.
- Open Internet Information Services (IIS) Manager ( Click Start >> Administrative Tools >> Internet Information Services (IIS) Manager).
- In the Connections pane, locate and click the server.
- In the server Home page (center pane) under the IIS section, double-click Server Certificates.
- In the Actions menu (right pane), click Complete Certificate Request.
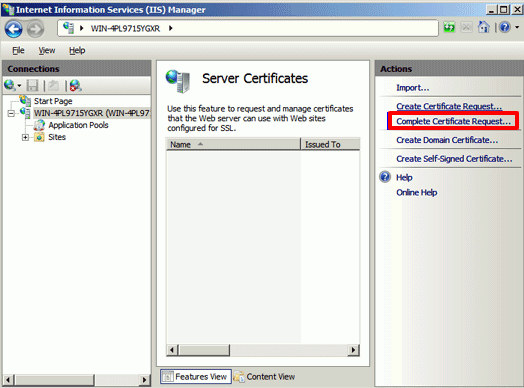
- In the Complete Certificate Request wizard, on the Specify Certificate Authority Response page, provide the following information:
| File name containing the certificate authority’s response: | Click the … button to locate the .cer file you received from your SSL provider (e.g., yourdomaincom.cer). |
| Friendly name: | Type a friendly name for the certificate. This is not part of the certificate; instead, it is used to identify the certificate. |
- Click OK to install the certificate.
- Now that you’ve successfully installed your SSL certificate, you need to configure your site to use it.
Step 5: Assign Your SSL Certificate
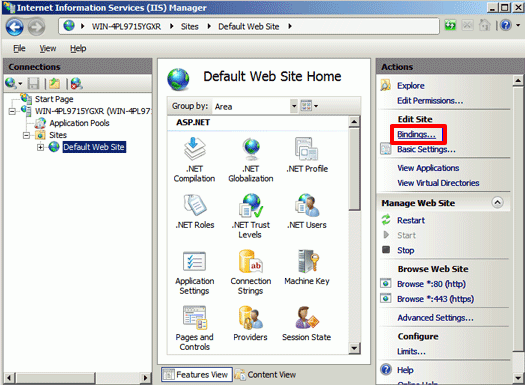
- In Internet Information Services (IIS) Manager, in the Connections pane, expand the name of the server on which the certificate was installed. Then expand Sites and click the site you want to secure using the SSL certificate.
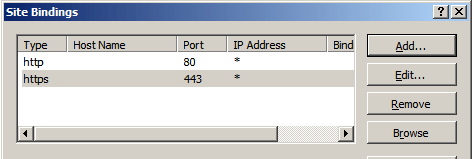
- In the Actions menu (right pane), click Bindings.
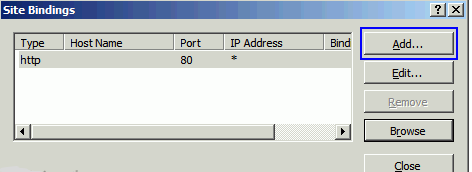
- In the Site Bindings window, click Add.
- In the Add Site Binding window, do the following and then click OK.
| Type: | In the drop-down list, select https. |
| IP address: | In the drop-down list, select the IP address of the site or select All Unassigned. |
| Port: | Type 443. (SSL uses port 443 to secure traffic.) |
| SSL certificate: | In the drop-down list, select your new SSL certificate (e.g., yourdomain.com). |
- Your SSL certificate is now installed, and the website is configured to accept secure connections.